The roles and role bindings are namespaced meaning they are created within namespaces. If you do not specify in namespace they are created in the default namespace and control access within the namespace.
In the namespace we can isolate resources like pods, deployments, and services. However, we can not isolate the nodes. The nodes are cluster-wide or cluster-scoped resources. They cannot be associated with any particular namespace. So the resources are categorized as either namespaced or cluster scoped. Thus, we need cluster roles and cluster roles binding
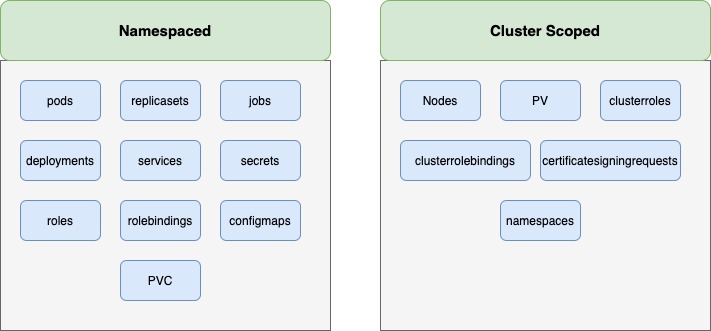
$ kubectl api-resources --namespaced=true
NAME SHORTNAMES APIGROUP NAMESPACED KIND
bindings true Binding
configmaps cm true ConfigMap
endpoints ep true Endpoints
events ev true Event
limitranges limits true LimitRange
persistentvolumeclaims pvc true PersistentVolumeClaim
pods po true Pod
podtemplates true PodTemplate
replicationcontrollers rc true ReplicationController
resourcequotas quota true ResourceQuota
secrets true Secret
serviceaccounts sa true ServiceAccount
services svc true Service
controllerrevisions apps true ControllerRevision
daemonsets ds apps true DaemonSet
deployments deploy apps true Deployment
replicasets rs apps true ReplicaSet
statefulsets sts apps true StatefulSet
localsubjectaccessreviews authorization.k8s.io true LocalSubjectAccessReview
horizontalpodautoscalers hpa autoscaling true HorizontalPodAutoscaler
cronjobs cj batch true CronJob
jobs batch true Job
stacks compose.docker.com true Stack
leases coordination.k8s.io true Lease
events ev events.k8s.io true Event
ingresses ing extensions true Ingress
ingresses ing networking.k8s.io true Ingress
networkpolicies netpol networking.k8s.io true NetworkPolicy
poddisruptionbudgets pdb policy true PodDisruptionBudget
rolebindings rbac.authorization.k8s.io true RoleBinding
roles rbac.authorization.k8s.io true Role$ kubectl api-resources --namespaced=false
NAME SHORTNAMES APIGROUP NAMESPACED KIND
componentstatuses cs false ComponentStatus
namespaces ns false Namespace
nodes no false Node
persistentvolumes pv false PersistentVolume
mutatingwebhookconfigurations admissionregistration.k8s.io false MutatingWebhookConfiguration
validatingwebhookconfigurations admissionregistration.k8s.io false ValidatingWebhookConfiguration
customresourcedefinitions crd,crds apiextensions.k8s.io false CustomResourceDefinition
apiservices apiregistration.k8s.io false APIService
tokenreviews authentication.k8s.io false TokenReview
selfsubjectaccessreviews authorization.k8s.io false SelfSubjectAccessReview
selfsubjectrulesreviews authorization.k8s.io false SelfSubjectRulesReview
subjectaccessreviews authorization.k8s.io false SubjectAccessReview
certificatesigningrequests csr certificates.k8s.io false CertificateSigningRequest
runtimeclasses node.k8s.io false RuntimeClass
podsecuritypolicies psp policy false PodSecurityPolicy
clusterrolebindings rbac.authorization.k8s.io false ClusterRoleBinding
clusterroles rbac.authorization.k8s.io false ClusterRole
priorityclasses pc scheduling.k8s.io false PriorityClass
csidrivers storage.k8s.io false CSIDriver
csinodes storage.k8s.io false CSINode
storageclasses sc storage.k8s.io false StorageClass
volumeattachments storage.k8s.io false VolumeAttachment
clusterroles
Cluster roles and cluster role bindings are just like roles except they are for a cluster scoped resources for example a cluster admin role can be created to provide a cluster administrator permissions to view create or delete nodes in a cluster.
The storage administrator role can be created to authorize a storage admin to create persistentvolumes
ClusterRole example
A ClusterRole can be used to grant the same permissions as a Role. Because ClusterRoles are cluster-scoped, you can also use them to grant access to:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
# "namespace" omitted since ClusterRoles are not namespaced
name: cluster-admin-example
rules:
- apiGroups: [""]
resources: ["nodes"]
verbs: ["list", "get", "create", "delete"]$ kubectl create -f cluster-admin-role.yaml
clusterrole.rbac.authorization.k8s.io/cluster-admin-example createdLink the cluster role binding the role binding object links the user to the role
ClusterRoleBinding example
To grant permissions across a whole cluster, you can use a ClusterRoleBinding. The following ClusterRoleBinding allows any user in the group “manager” to read secrets in any namespace.
apiVersion: rbac.authorization.k8s.io/v1
# This cluster role binding allows anyone in the "manager" group to read secrets in any namespace.
kind: ClusterRoleBinding
metadata:
name: cluster-admin-role-binding-example
subjects:
- kind: User
name: cluster-admin # Name is case sensitive
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: cluster-admin-example
apiGroup: rbac.authorization.k8s.io$ kubectl create -f cluster-admin-role-binding.yaml
clusterrolebinding.rbac.authorization.k8s.io/cluster-admin-role-binding-example createdAdditionally, you can create a cluster role for namespace resources as well. When you do that the user will have access to these resources across all nameapaces.
- Roles: a user to access objects like pods the user had access to the pods in a particular namespace.
- Cluster Rules. when you authorize a user to access the objects like pods the user gets access to all pods across the cluster. Kubernetes creates a number od cluster roles by default.
View clusterroles and clusterrolebinding
$ kubectl get clusterroleNAME AGE
admin 81d
cluster-admin 81d
cluster-admin-example 11m
compose-service 81d
compose-stack-admin 81d
compose-stack-edit 81d
compose-stack-view 81d
edit 81d
system:aggregate-to-admin 81d
system:aggregate-to-edit 81d
system:aggregate-to-view 81d
system:auth-delegator 81d
system:basic-user 81d
system:certificates.k8s.io:certificatesigningrequests:nodeclient 81d
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 81d
system:controller:attachdetach-controller 81d
system:controller:certificate-controller 81d
system:controller:clusterrole-aggregation-controller 81d
system:controller:cronjob-controller 81d
system:controller:daemon-set-controller 81d
system:controller:deployment-controller 81d
system:controller:disruption-controller 81d
system:controller:endpoint-controller 81d
system:controller:expand-controller 81d
system:controller:generic-garbage-collector 81d
system:controller:horizontal-pod-autoscaler 81d
system:controller:job-controller 81d
system:controller:namespace-controller 81d
system:controller:node-controller 81d
system:controller:persistent-volume-binder 81d
system:controller:pod-garbage-collector 81d
system:controller:pv-protection-controller 81d
system:controller:pvc-protection-controller 81d
system:controller:replicaset-controller 81d
system:controller:replication-controller 81d
system:controller:resourcequota-controller 81d
system:controller:route-controller 81d
system:controller:service-account-controller 81d
system:controller:service-controller 81d
system:controller:statefulset-controller 81d
system:controller:ttl-controller 81d
system:coredns 81d
system:csi-external-attacher 81d
system:csi-external-provisioner 81d
system:discovery 81d
system:heapster 81d
system:kube-aggregator 81d
system:kube-controller-manager 81d
system:kube-dns 81d
system:kube-scheduler 81d
system:kubelet-api-admin 81d
system:node 81d
system:node-bootstrapper 81d
system:node-problem-detector 81d
system:node-proxier 81d
system:persistent-volume-provisioner 81d
system:public-info-viewer 81d
system:volume-scheduler 81d
view 81d
vpnkit-controller 81d
$ kubectl get clusterrolebinding
NAME AGE
cluster-admin 81d
cluster-admin-role-binding-example 5m31s
compose 81d
compose-auth-delegator 81d
compose-auth-view 81d
docker-for-desktop-binding 81d
kubeadm:kubelet-bootstrap 81d
kubeadm:node-autoapprove-bootstrap 81d
kubeadm:node-autoapprove-certificate-rotation 81d
kubeadm:node-proxier 81d
storage-provisioner 81d
system:basic-user 81d
system:controller:attachdetach-controller 81d
system:controller:certificate-controller 81d
system:controller:clusterrole-aggregation-controller 81d
system:controller:cronjob-controller 81d
system:controller:daemon-set-controller 81d
system:controller:deployment-controller 81d
system:controller:disruption-controller 81d
system:controller:endpoint-controller 81d
system:controller:expand-controller 81d
system:controller:generic-garbage-collector 81d
system:controller:horizontal-pod-autoscaler 81d
system:controller:job-controller 81d
system:controller:namespace-controller 81d
system:controller:node-controller 81d
system:controller:persistent-volume-binder 81d
system:controller:pod-garbage-collector 81d
system:controller:pv-protection-controller 81d
system:controller:pvc-protection-controller 81d
system:controller:replicaset-controller 81d
system:controller:replication-controller 81d
system:controller:resourcequota-controller 81d
system:controller:route-controller 81d
system:controller:service-account-controller 81d
system:controller:service-controller 81d
system:controller:statefulset-controller 81d
system:controller:ttl-controller 81d
system:coredns 81d
system:discovery 81d
system:kube-controller-manager 81d
system:kube-dns 81d
system:kube-scheduler 81d
system:node 81d
system:node-proxier 81d
system:public-info-viewer 81d
system:volume-scheduler 81d
vpnkit-controller 81d