Network Namespaces are used by containers like Docker to implement network isolation.
Containers are separated from the underlying host using namespace.
When you create a container, you want to make sure that it is isolated, that it does not see any other processes on the host or any other containers. So we create a namespace on the host. The container is concerned, it only sees the processes run by it and thinks that it is on its own host.
When it comes to networking, our host has its own interfaces that connect to the local area network. Our host has its own routing and our tables with information about the rest of the network. When the container is created, we create a network namespace for it, that way it has no visibility to any network-related information on the host. Within its namespace, the container can have its own virtual interfaces, routing, and other tables.
To create a new network namespace on a Linux host,
# create network namespace
$ ip netns add red
$ ip netns add blue
# check the namespace
$ ip netns
blue
redTo list the interfaces on the host.
$ ip link
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000
link/ether 08:00:27:42:3d:82 brd ff:ff:ff:ff:ff:ffhow do we run the same command within the created namespace?
$ ip netns exec red ip link
1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
ip -n red link
1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00With network namespaces, we have successfully prevented the container from seeing the host’s interface.
Within the network namespace, there is no network connectivity, they have no interfaces of their own, and they cannot see the underlying host network.
How to check the entries and routing table of machine?
$ arp
Address HWtype HWaddress Flags Mask Iface
_gateway ether 52:54:00:12:35:02 C enp0s3
$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default _gateway 0.0.0.0 UG 100 0 0 enp0s3
10.0.2.0 0.0.0.0 255.255.255.0 U 100 0 0 enp0s3
link-local 0.0.0.0 255.255.0.0 U 1000 0 0 enp0s3Inside the namespace
$ ip netns exec red arp
# Now no entry
$ ip netns exec red route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Ifacehttp://manpages.ubuntu.com/manpages/trusty/man8/ip-netns.8.html
You can link two network namespaces
$ ip link add veth-red type veth peer name veth-blue
$ ip link set veth-red netns red
$ ip link set veth-blue netns blue
$ ip -n red addr add 192.168.15.1/24 dev veth-red
$ ip -n blue addr add 192.168.15.2/24 dev veth-blue
$ ip -n red link set veth-red up
$ ip -n blue link set veth-blue up
$ ip netns exec red ping 192.168.15.2
PING 192.168.15.2 (192.168.15.2) 56(84) bytes of data.
64 bytes from 192.168.15.2: icmp_seq=1 ttl=64 time=0.039 ms
64 bytes from 192.168.15.2: icmp_seq=2 ttl=64 time=0.045 ms
64 bytes from 192.168.15.2: icmp_seq=3 ttl=64 time=0.031 ms
64 bytes from 192.168.15.2: icmp_seq=4 ttl=64 time=0.042 ms
Delete Link pair
$ ip -n red link del veth-red
$ ip -n blue link del veth-blue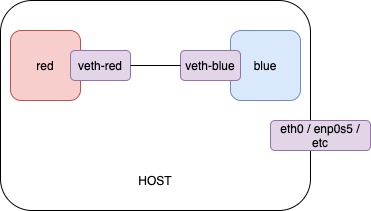
# ARP Tables
$ ip netns exec red arp
Address HWtype HWaddress Flags Mask Iface
192.168.15.2 ether 52:4f:9d:4d:1d:6a C veth-red
$ ip netns exec blue arp
Address HWtype HWaddress Flags Mask Iface
192.168.15.1 ether 3a:b7:64:24:aa:6e C veth-blue
$ ip netns exec blue route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.15.0 0.0.0.0 255.255.255.0 U 0 0 0 veth-blue
$ ip netns exec red route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.15.0 0.0.0.0 255.255.255.0 U 0 0 0 veth-redIf there are more than two namespace, you need a virtual network inside host. Create a network you need a switch. However, create virtual network you need a virtual switch. So you create a virtual switch within our host and connect the namespace us to it.
How do you create a virtual switch between the host?
There are some solutions (Linux bridge, Open vSwitch, etc). To create an internal bridge network, we add a new interface to the host using the ip link
Using ip addr flush will work, but it will also clear any and all addresses set on that interface – possibly including the one that you are using, if you’re logged in to a remote machine. This may lock you out of your device.
RNETLINK answers: File exists happens when you’re trying to add a rule that conflicts with an existing rule. I would guess that OP was encountering this because they had already set the address with ifconfig. This error can usually be resolved by converting the add command to a similarly structured change or replace command.
It’s much safer to use ip addr change or ip addr replace instead.
$ ip link add v-net-0 type bridge
// Our host is concerned, it is just another interface.
$ ip link
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000
link/ether 08:00:27:42:3d:82 brd ff:ff:ff:ff:ff:ff
5: v-net-0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT group default qlen 1000
link/ether 66:e3:0a:e2:fe:b1 brd ff:ff:ff:ff:ff:ff
$ ip link set dev v-net-0 up
$ ip link add veth-red type veth peer name veth-red-br
$ ip link add veth-blue type veth peer name veth-blue-br
$ ip link set veth-red netns red
$ ip link set veth-red-br master v-net-0
$ ip link set veth-blue netns blue
$ ip link set veth-blue-br master v-net-0
$ ip -n red addr add 192.168.15.1/24 dev veth-red
$ ip -n blue addr add 192.168.15.2/24 dev veth-blue
$ ip -n red link set veth-red up
$ ip -n blue link set veth-blue up
// Add bridge ip address
$ ip addr add 192.168.15.5/24 dev v-net-0Check ARP and Route
# ARP Tables
$ ip netns exec red arp
$ ip netns exec blue arp
# Kernel IP routing table
$ ip netns exec blue route
$ ip netns exec red routeNow you can ping red namespace in our Localhost
ping 192.168.15.1The virtual switch also need the gateway to access outside world.
The localhost is the gateway that connects the two networks
What is a system that has one interface on the network local to the namespace.
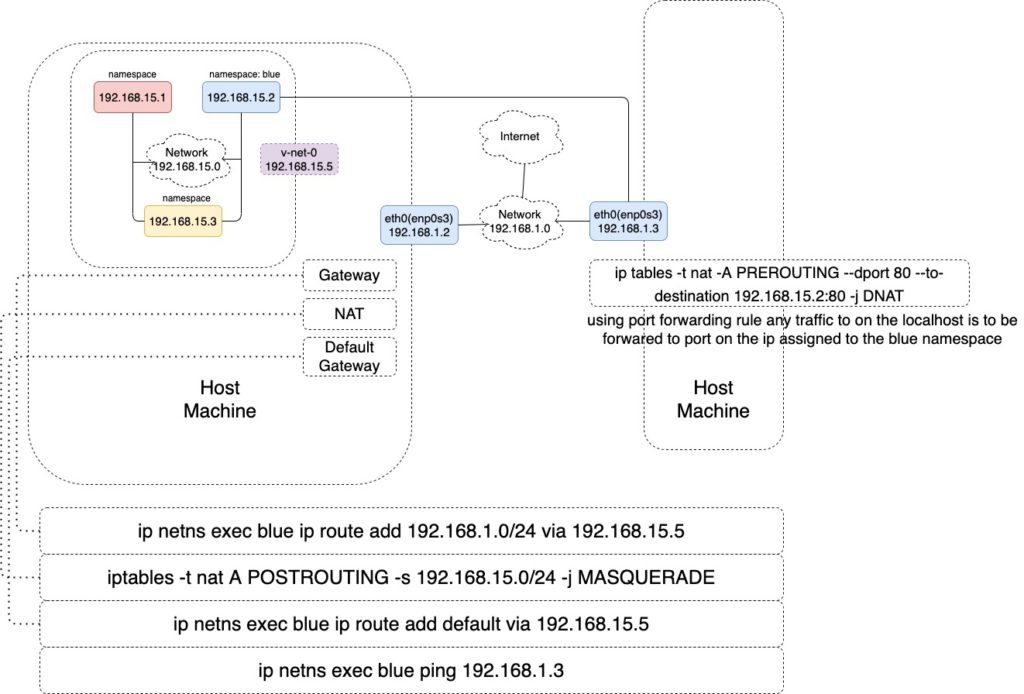
blue namespace to reach outside.
$ ip netns exec blue ip route add 192.168.1.0/24 via 192.168.15.5$ iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -j MASQUERADEblue namespace to reach to internet.
$ ip netns exec blue ip route add default via 192.168.15.5Another private machine reaches blue namespace network.
ip tables -t nat -A PREROUTING --dport 80 --to-destination 192.168.15.2:80 -j DNAT//another host machine
$ ip netns exec blue ping 192.168.1.3
// on internet
ip netns exec blue ping 8.8.8.8Basic information
Routing table
In computer networking a routing table, or routing information base, is a data table stored in a router or a network host that lists the routes to particular network destinations, and in some cases, metrics associated with those routes
Address Resolution Protocol (ARP)
The Address Resolution Protocol (ARP) is a communication protocol used for discovering the link-layer address, such as a MAC address, associated with a given internet layer address, typically an IPv4 address. This mapping is a critical function in the Internet protocol suite.
$ arp
Address HWtype HWaddress Flags Mask Iface
_gateway ether 00:1c:42:00:00:18 C enp0s5